You’ve likely encountered CAPTCHAs (Completely Automated Public Turing test to tell Computers and Humans Apart), check boxes that are designed to differentiate humans from bots by presenting challenges that are easy for humans but difficult for machines. CAPTCHAs are commonly used by websites and online services to verify users. However, cybercriminals are now using fake CAPTCHAs to trick you into infecting your computer with malware that steals your sensitive information.
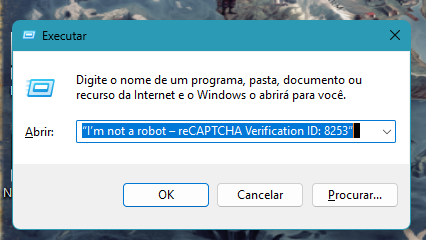
Fake CAPTCHAs typically appear on compromised websites, often promising access to pirated movies and music. Instead of a simple verification, these CAPTCHAs ask you to perform unusual “verification steps” that involve copying and pasting commands into the Windows Run dialog box (accessed by pressing Windows key + R). The Windows Run dialog box allows users to execute commands directly in the operating system.
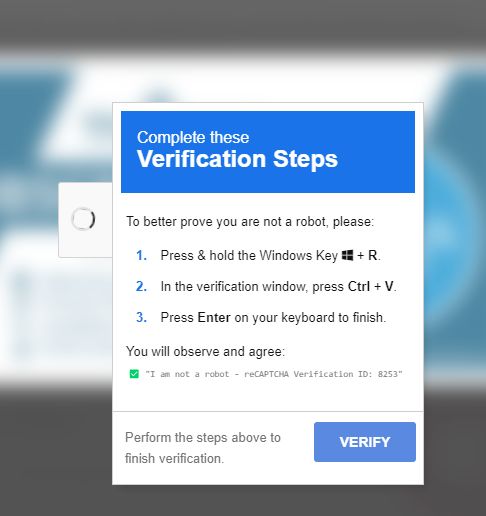
By following these instructions, you’re actually executing malicious code that downloads and installs information-stealing malware.
This malware can steal passwords, cookies, cryptocurrency wallet details, and other sensitive data. Understanding how to identify these fraudulent CAPTCHAs and take preventive measures is critical for safeguarding your data.
How fake CAPTCHAs work
The CAPTCHA instructs the user to paste a command into the Windows Run dialog box—a tool used to execute commands directly in the operating system—that often utilizes mshta.exe, a legitimate Windows binary designed to run HTML applications, which attackers exploit to download and execute malicious files from remote servers.
These files appear harmless, with extensions like .mp3 or .jpg, but they contain encoded scripts that execute PowerShell commands in the background. PowerShell is a scripting tool used for automating tasks in Windows, but attackers can use it to execute malicious scripts. These commands bypass browser-based defenses by running outside the browser context, making detection more challenging.
The PowerShell scripts typically go through multiple stages of decryption and execution, ultimately delivering infostealers. These malware programs exfiltrate sensitive data and may even deploy additional payloads to maintain persistence on the victim’s system.
Examples of fake CAPTCHA: Lumma Stealer and Vidar Stealer
To better understand how fake CAPTCHAs are used to distribute malware, let’s look at examples like Lumma Stealer and Vidar Stealer, which are sophisticated malware programs designed to steal sensitive information from compromised systems.
Lumma Stealer has been active since at least 2022 and operates under the malware-as-a-service (MaaS) model, allowing cybercriminals to rent or purchase its capabilities for their own attacks. It is frequently distributed through various methods, including fake CAPTCHA pages, cracked software, Discord CDN links, and malvertising campaigns.
Lumma’s infection chain involves multiple stages of obfuscation and decryption, bypassing security controls like Windows Antimalware Scan Interface (AMSI), a Windows feature designed to detect and block malicious scripts. It is known for its ability to evade detection through process hollowing, a technique where malware injects malicious code into legitimate processes to avoid detection, and payload obfuscation techniques.
Vidar Stealer is often distributed alongside other malware in campaigns involving phishing emails, cracked software, or malicious websites. Vidar is capable of exfiltrating sensitive data while maintaining persistence on infected systems. The attack chain typically begins with a fake CAPTCHA prompt instructing users to execute PowerShell commands under the guise of human verification. These commands initiate a multi-stage infection process that decrypts additional payloads before deploying Vidar.
What to do if your device is compromised
If you suspect you’ve interacted with a fake CAPTCHA and followed its instructions, leaving your device and your data exposed, then follow these steps:
- Run a full malware scan: Use a reputable anti-malware program to scan your system and remove any detected threats.
- Change passwords: Change passwords for all your important accounts, including email, banking, and social media. To increase security, add multi-factor authentication to all your accounts.
- Contact cybersecurity experts: Seek assistance from professional malware removal services such as Porthas to ensure the malware is completely removed from your device.
Report the incident: Contact the Internet Crime Complaint Center (IC3) and report the incident with as many details as possible to help law enforcement track down the perpetrators.








